Cyber Security Services
Cyber threat in Australia over the past 12 months has significantly increased. There have been small and large organisations that have been breached resulting in significant pain.
REDD has invested in highly skilled resources, both internally and using industry best partners, to ensure you receive the best possible security aligned to your specific needs.
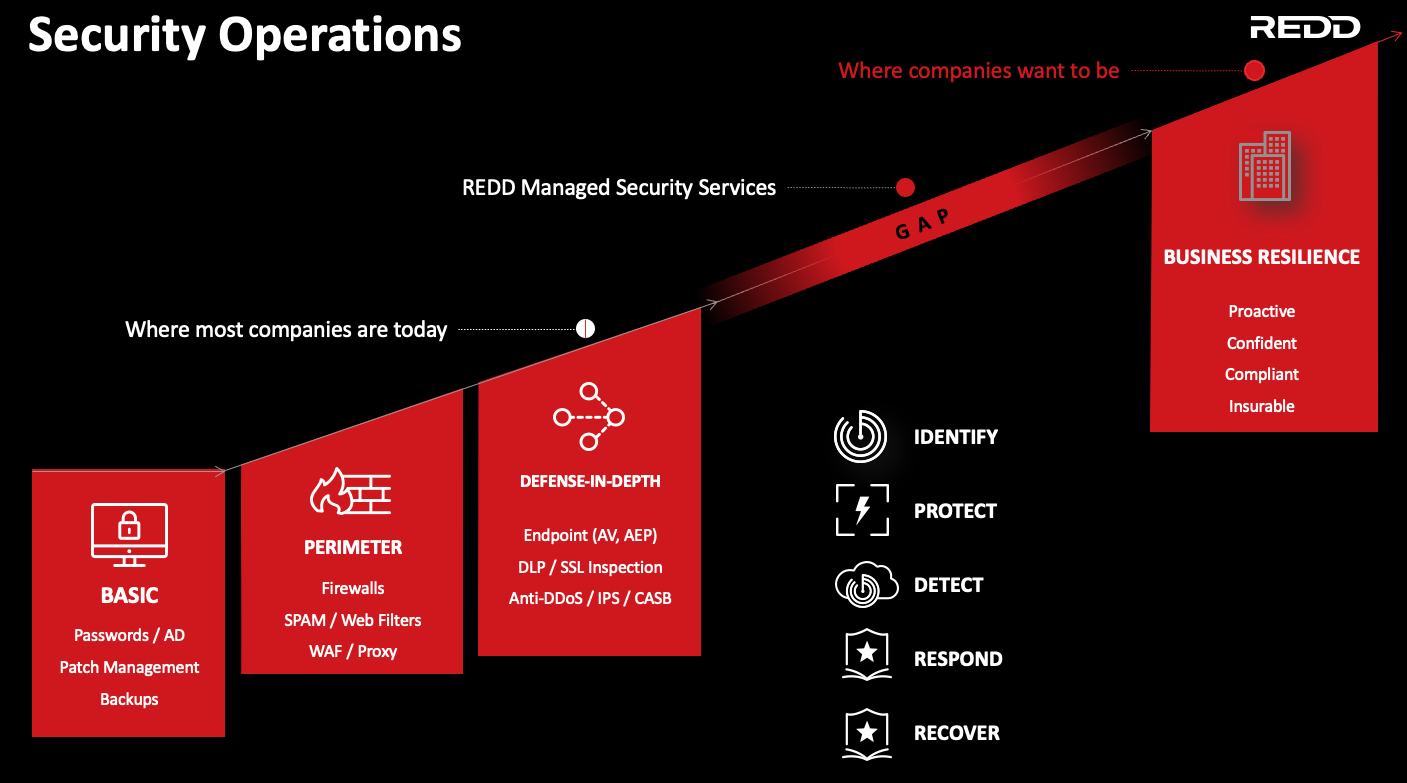
As the above image describes, cyber security is evolving past Anti Virus, Firewalls and spam filters, although these are still critical.
REDD takes cyber threats, your business and your data seriously!
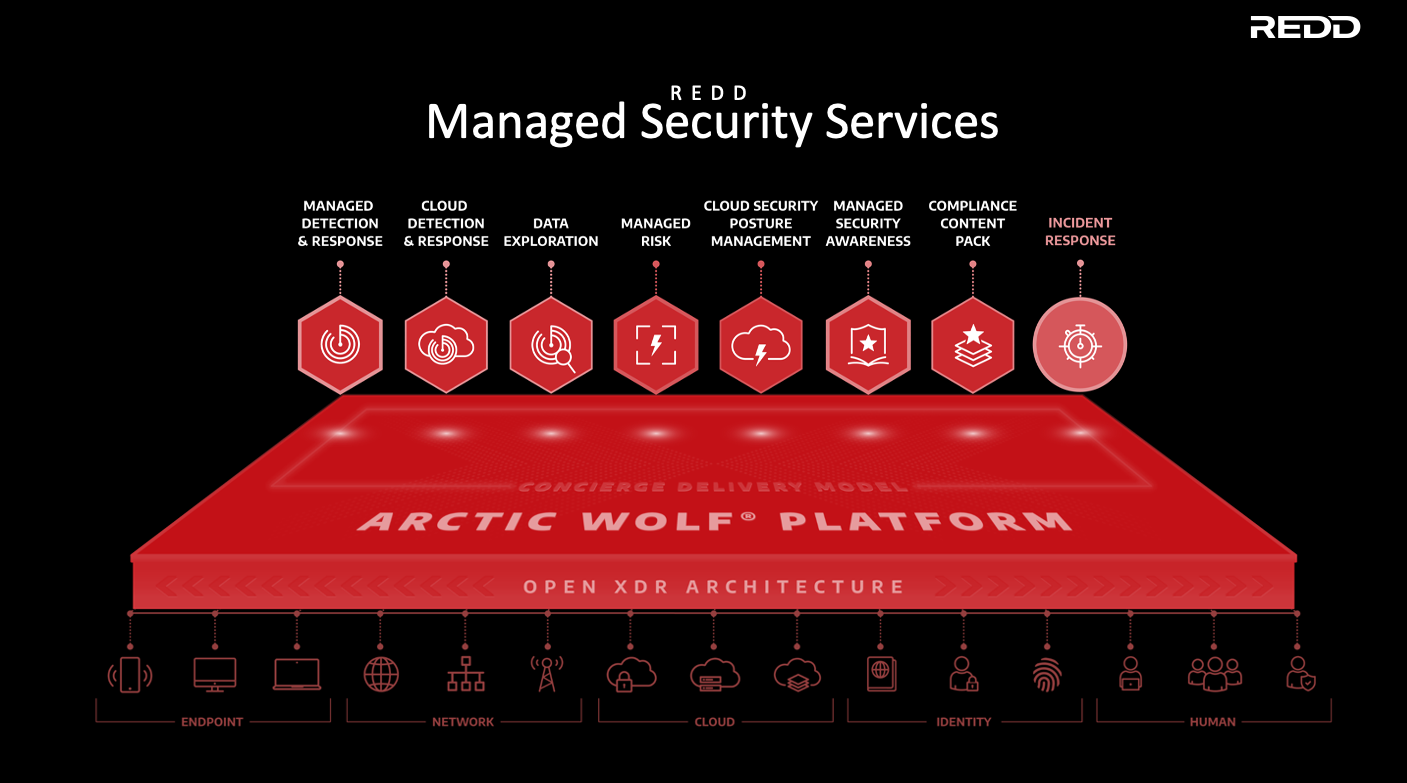
Separate to this, businesses need some level of threat detection & response watching their data 24x7, Detecting, Responding, Recovering, Identifying and Protecting. To help mitigate cyber risk, we have launched three levels of threat detection across our Managed Security Services divisions.
24x7 security monitoring by SOC (Security Operations Center), Customised Alerting, Customised security monthly and quarterly reporting, Incident Response team with guided remediation & Root cause analysis, Threat hunting, plus a 90 day log retention
Managed Detection & Response
Continuous vulnerability scanning, Comprehensive risk profiling, Proactive notifications and alerts, Actionable monthly reporting, Monthly Internal, External & host-based Vulnerability Scans
Managed Risk
Fully Managed Cyber Awareness Program, Employee friction free user experience & Positive education and reinforcement, Ongoing Microlearning, 24x7 Account takeover monitoring, Integrated phishing simulations, Performance Analytics
Managed Security Awareness
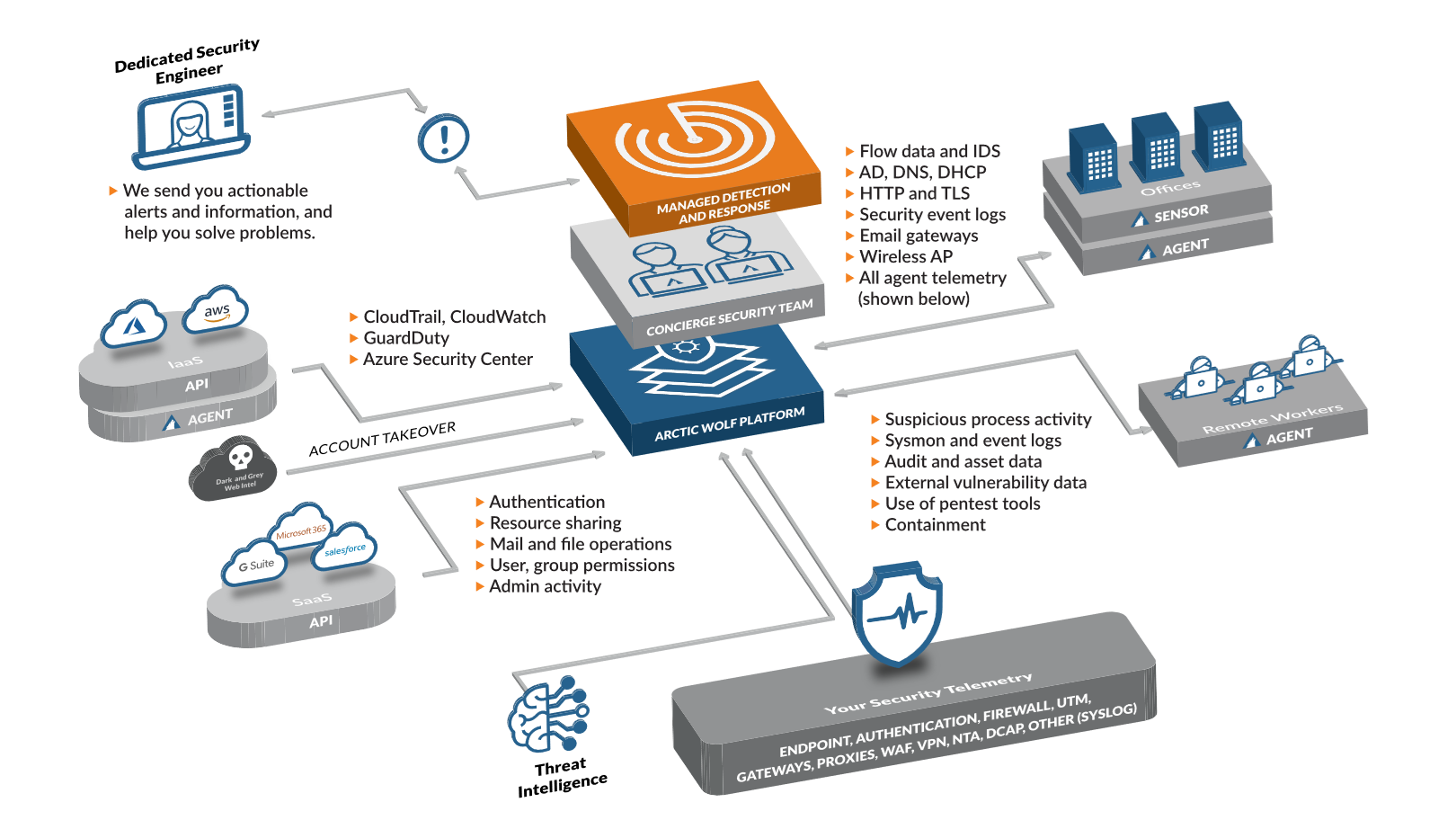
Above outlines REDD's Security Operations Framework
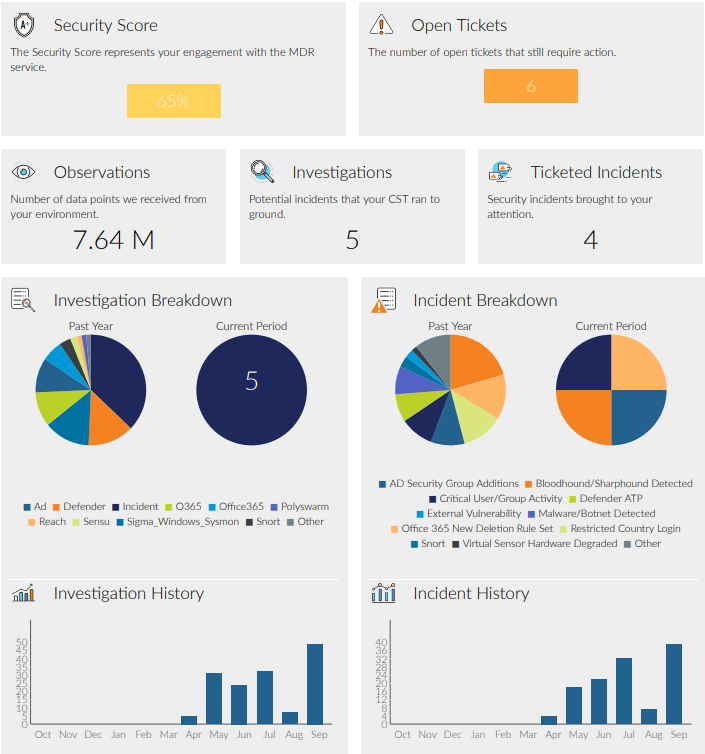
See above example one page executive security report we provide you each month

REDD provides Penetration Testing to help ensure your systems and environment has identified holes to enable swift remediation BEFORE a cyber breach could occur.
Managed Cyber Security Services
REDD's Managed Security Services (MSS) provides piece of mind through access to our 24x7 Security Operation Centre (SOC). This offering works with all of your existing infrastructure, endpoints and hosted environments - all attack surfaces, traffic and changes are logged and collected into our hosted SIEM Software. Meaning that your businesses data is being monitored around the clock by the team at REDD.
Managed Detection Response
REDD's Managed Detection and Response (MDR) solution leverages your existing tech stack to identify advanced network, endpoint and cloud threats. This solution provides 24/7 monitoring to help you detect, respond and recover from modern cyber attacks.
Managed Awareness
The human firewall is the most critical line of defense. REDD's Managed Security Awareness prepares your employees to identify and stop social engineering attacks, like phishing scams—helping to end cyber risk at your organisation.
Cyber Security Frameworks
The Australian Cyber Security Centre (ACSC) has developed prioritised mitigation strategies, in the form of the Strategies to Mitigate Cyber Security Incidents, to help organisations protect themselves against various cyber threats. The most effective of these mitigation strategies are the Essential Eight.



